
Data centers are among the most complex and difficult facilities to secure, and a prized target for hackers
attempting to disrupt a myriad of commercial, industrial and other online activities. Like any other facility security
project, data center security combines physical and software security, that apply to both server operation and
supporting systems – cooling, power supply, etc.
A leading data-center operator in EMEA with multiple facilities over 25,000 square meters experienced some
interruptions in their internal IT network due to unsupervised work of 3rd party technicians. They then realized
that though their data-center is equipped with a high-end building control system which applies 24×7 monitoring
and control to all the building’s infrastructure, it is actually quite vulnerable from the cyber point of view as it is
connected to the IT network infrastructure. They launched an urgent OT cyber security project that included both
IT-OT network segmentation as well as OT network asset mapping and anomaly detection.
The main objective stated by the customer was hardening the security of the server systems, and creating a framework for in-house operators to monitor the network and receive alerts upon network traffic exceptions:
• Securing the facility’s power supply (IEC61850)
• Securing the server cooling system
• Strengthening the segmentation between building and operational systems.
• Creating a visual OT network map
• Setting up a system for presenting supply-chain attacks that may threaten the data center through equipment vendors’ maintenance activities
The first step in the project was meeting with the customer to determine their objectives and learning about the nature and the specifics of the IT-OT network at the data center.
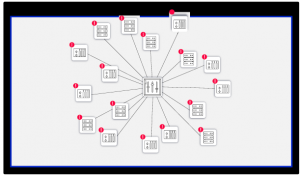
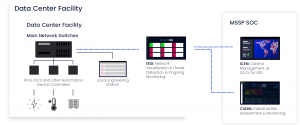
Next, a network model (digital image) of the OT network was created. This was done using the iSID threat detection & monitoring platform, by analyzing a representative amount of data traffic, recorded using a parallel data stream (as to not disrupt operations) from the facilities main data switch.
Once completed, iSID was able to provide a detailed network model, including all assets, firmware, ports, open connections and protocols and vulnerabilities/risks associated with different assets.
Once complete, the iSID-generated digital image was reviewed by Radiflow’s cyber experts, in tandem with the customer, and modified to reflect network attributes that couldn’t be detected programatically.
Once all unnecessary open ports and unnecessary protocols were handled, the model was deemed complete and suitable for reflecting the network’s baseline activity, as well as for use as a visual network map, down-drillable to each and every device’s full properties, links and vulnerabilities.
At the same time, iSID automatically created a logical business unit model, each with different security needs. These business processes, also reflected in the network map, allow applying different communication, asset and protocol rules in iSID, depending on criticality.
Using rule-based alerts for specific devices, iSID created a central monitoring point for critical systems, with alerts for exceeding different sensor or controller values, as well as changes to controller logic or adding devices to the network.
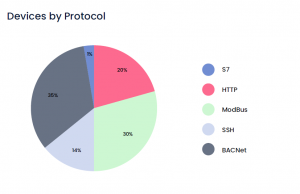
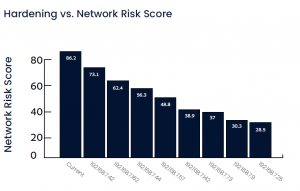
At present, Radiflow’s system is fully operational in one data center facility and is being considered for additional data centers operated by the customer.

One Weak Password, Full Process Control: Inside Norway’s 2025 Dam Cyberattack

Project Management in OT/ICS Projects with IEC 62443 and MITRE ATT&CK using Radiflow

Rogue Communication Modules in Solar Inverters: Radiflow Threat Analysis