The entry point? A single weak password—either guessed or obtained from previously leaked credentials. Without multi-factor authentication (MFA) in place and operating on a flat network architecture, attackers were able to move laterally across systems with ease, encrypting critical data and paralyzing the company’s operations.
Despite having cyber insurance and meeting basic compliance standards, KNP had no viable recovery path. Within weeks, the business collapsed. Over 700 employees were laid off, and a century and a half of history vanished due to simple, avoidable security failures.
What’s most alarming is that this wasn’t the result of an advanced nation-state campaign or a zero-day exploit. It was a basic case of credential misuse and poor network design—exactly the kind of weaknesses that plague countless organizations today.
And those vulnerabilities? They’re not just limited to IT networks. They’re even more pervasive in Operational Technology (OT) environments, where legacy systems, direct process control, and high uptime demands often sideline cybersecurity. In OT, a single exposed interface or shared password doesn’t just threaten data—it can shut down plants, flood reservoirs, or disrupt public services.
Earlier this year, a cyberattack on Norway’s Lake Risevatnet dam offered a chilling real-world example of how simple security lapses in OT can lead to serious physical consequences. A publicly accessible Human-Machine Interface (HMI), protected only by a weak password, allowed attackers to remotely open a dam valve to 100%, releasing hundreds of liters per second of water for hours before it was manually shut off.
No malware. No zero-day exploits. Just a discoverable internet-facing device and poor password hygiene. Read the full case study
The security failures that took down KNP Transport are far from unique—and in Operational Technology (OT) environments, they’re often even more widespread. Attackers aren’t using sophisticated exploits; they’re taking advantage of the same old weaknesses, and they work just as well (if not better) in OT.
These aren’t edge cases—they’re everyday realities, especially in mid-sized OT organizations where legacy infrastructure and limited budgets make security a challenge. And while these environments might not seem like obvious targets, attackers know they often lack the visibility and defenses needed to stop even basic intrusion attempts.
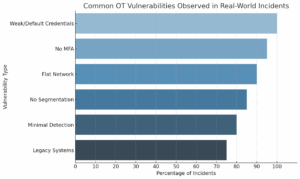
To mitigate the risk of cyberattacks, OT organizations must extend their focus beyond compliance checklists. The good news? Many of the most effective improvements are straightforward and high-impact.
Here’s where to start:
Access control is the first—and often weakest—line of defense.
A flat network gives attackers freedom to roam. Segmentation stops them in their tracks.
Why it matters: Even if attackers get in, segmentation limits their reach and buys your team time to respond.
You can’t stop what you can’t see.
Why it matters: The earlier you detect unusual activity, the faster you can contain it—before physical processes are affected.
When things go wrong, a fast, coordinated response is the difference between a disruption and a disaster.
Why it matters: Many OT systems can’t simply be restored from backups like IT environments. Response planning must reflect real-world constraints like manual intervention and safety protocols.
By focusing on these four areas, OT environments—especially mid-sized ones—can make significant strides in resilience, even with limited resources. The goal isn’t perfection—it’s progress that prevents catastrophe.
Prompt, automatic, accurate, and compliant risk assessments for CNI and ICS Operators and their MSSPs, Auditors, and Consultants.
The collapse of KNP Transport is a sobering reminder that it doesn’t take a sophisticated cyberattack to dismantle a business—just a weak password, no MFA, and a flat network. The Norway dam cyberattack drives that point even further: In Operational Technology, those same weaknesses don’t just lock you out—they put real-world systems, safety, and communities at risk.
In both cases, the organizations weren’t massive global players. They were mid-sized enterprises, operating under the dangerous assumption that “we’re too small to be a target.” That assumption is no longer just wrong—it’s proven false.
Attackers are actively scanning for exposed interfaces, unsegmented networks, and OT systems protected by nothing more than outdated credentials. And once they’re in, the consequences escalate fast—from encrypted files to open floodgates.
In OT, you don’t get the luxury of time. The margin between detection and disaster is narrow. But the opportunity to act is still here—before the breach, not after.


Hacktivists Are Hijacking Exposed ICS Devices — Here’s What Every Operator Must Know

The JLR Cyber Incident: A Wake-Up Call for Manufacturing Resilience

New Radiflow360 platform to offer visibility, control across OT cybersecurity lifecycle