Earlier this month, global tire manufacturer Bridgestone experienced a cyber incident that temporarily halted operations at two South Carolina plants and one in Quebec. Described as a “limited cyber incident”, the company responded swiftly and confirmed that no customer data or interfaces were affected.
While production was restored quickly, the implications go far beyond these individual sites. Even a contained disruption like this one signals a clear and growing threat to industrial systems—especially those that rely heavily on legacy OT (Operational Technology) infrastructure.
Bridgestone’s response was commendable, but it also illustrates a deeper truth: you don’t need a full-blown data breach to suffer significant operational and reputational consequences.
In OT environments:
And in industries like automotive manufacturing, where uptime is paramount, even “minor” events can cascade into customer dissatisfaction, contractual penalties, and revenue loss.
The Bridgestone incident highlights the urgent need for a structured cybersecurity approach—not just in defense, but in preparation, detection, and resilience. These five foundational pillars offer a framework any industrial organization can adopt:
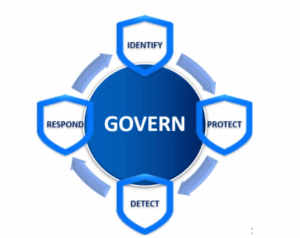
| Pillar | Key Action | Outcome |
| 1. Identify What You Have | Continuous, passive asset discovery across your ICS/OT network | A real-time inventory allows you to prioritize risk accurately |
| 2. Protect What Matters Most | Enforce granular segmentation and policy controls on critical systems | Reduced attack surface and robust containment if compromise occurs |
| 3. Detect Threats as They Happen | Deploy passive OT-specific anomaly detection (e.g., Radiflow iSID) | Early warning for intrusions without interrupting operations |
| 4. Respond with OT-Aware Playbooks | Automate incident response tailored to OT protocols | Faster containment, minimized downtime, and structured recovery |
| 5. Govern and Align with Regulation | Map controls to standards like NIST, IEC 62443, and local mandates | Ensure cyber readiness and pass audits with confidence |
Cyber incidents in OT are no longer rare—they’re routine. From Colonial Pipeline to JBS Foods to Bridgestone, no sector is immune. Yet many facilities still assume “it won’t happen here,” leaving critical infrastructure exposed.
OT cybersecurity must now be viewed as part of business continuity, safety, and resilience. The time to act is before an incident occurs: know your assets, control access, build response plans, and turn awareness into action.


Renewable Energy Cybersecurity Wake‑Up Call: What Poland’s 29 December 2025 Incident Should Change

Hacktivists Are Hijacking Exposed ICS Devices — Here’s What Every Operator Must Know

The JLR Cyber Incident: A Wake-Up Call for Manufacturing Resilience