The viability of any project or task is directly linked to the value it produces, i.e. if value exceeds costs, the project is worthwhile; otherwise, it’s a losing proposition.
Applying this simple model to cyber-security, and namely to OT-security, presents the problem: how do you determine the value of an OT-security system that successfully protects the industrial network? The costs of securing the OT network are known, but what are they measured against?
One solution is to rely on industry and regional benchmarks: find out what equivalent companies (by industry, size, locale, etc.) had invested in, and replicate their system. While this crude method of planning (and obviously I’m over-simplifying) leaves out many of the network and the company’s unique characteristics – no two industrial networks face the same threats or employ the same devices – it allows you, with just the right amount of customization, to bring your OT security “within the (very large) ballpark” of your reference group’s OT systems’ value. Plus, in lieu of a better option, it’s the best you got.
In time, and as the field of OT security matured, better ways to calculate the value of OT security were developed. The ARC Advisory Group’s formulation of the different stages of cyber-security maturity describes this evolution as transitioning from Vulnerability Management – installing passive defence systems that identify vulnerabilities in the OT network along with effective matching protections, to Threat Management – installing active defence mechanisms that react to the entire security environment, including threat agent capabilities, the user organization’s security needs, per-business unit security, and more. (Much of the principles of Active Defence and its implementation as Risk Management are embedded into the IEC 62443 standard, which in many ways represents the maturing of OT security).
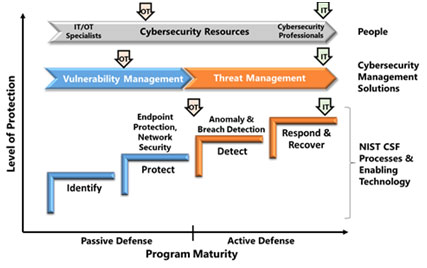
The ARC Advisory Group’s model for OT security maturityThe introduction of Risk Management as an overarching method of benchmarking, planning and monitoring the effectiveness (read: value) of the OT security system allows for a much higher level of optimization, meaning that you get the most security for every dollar spent.
This is done by re-defining the role of the OT security system: from merely identifying vulnerabilities and installing protections that prevent them from materializing as cyber-attacks, to minimizing the impact – the damages to the organization and its people – of a successful cyber-attack.
This is based on a number of underlying assumptions and guidelines:
Given the above, a network’s total risk can be formulated as the aggregate of the impact of a successful attack on each business unit, weighted by probability of each such attack materializing.

This equation relies on multiple inputs, both intrinsic and extrinsic to the OT network:
Given these multiple, vast datasets, there’s an obvious need for a methodological risk management process that’s able to produce actionable decision-making information for CISOs and other business stakeholders (CRO, OT manager) responsible for business continuity. This includes key indicators, comprehensive security reports, and a highly optimized OT security roadmap that mitigates the most risk per dollar spent.
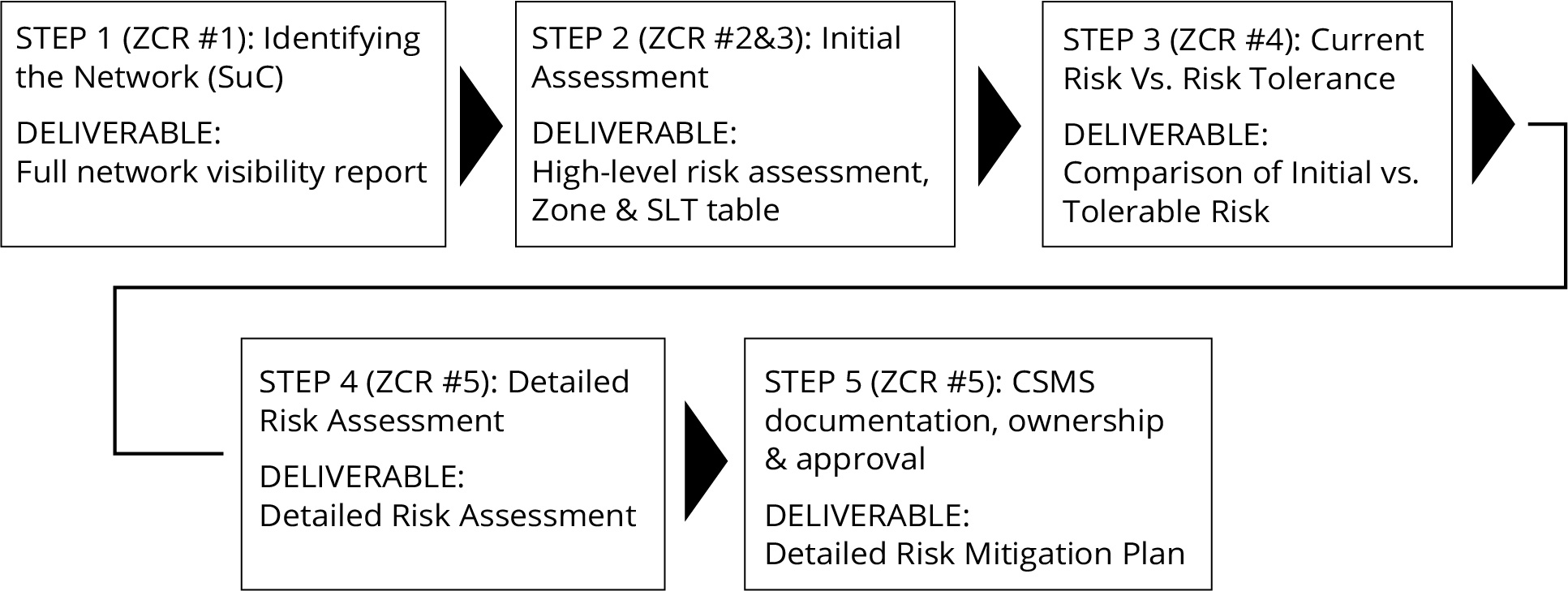
The added value of risk assessment (using Radiflow CIARA)
Radiflow’s CIARA is the first-of-its-kind automated, fully-IEC 62443 compliant risk assessment and management platform for industrial networks.
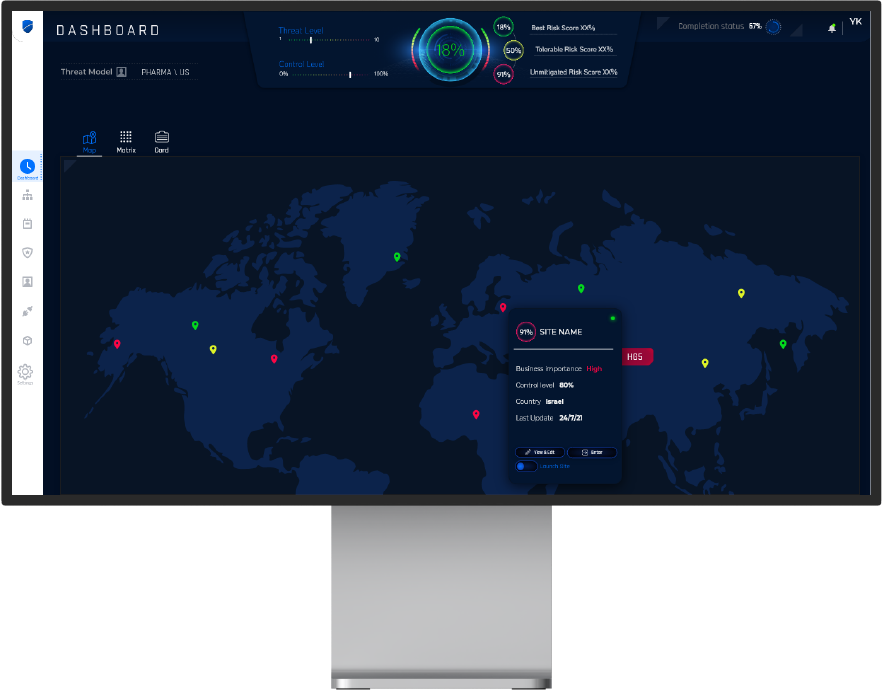
To assess the risk posture of an OT network, CIARA uses a self-learned, non-destructive digital image of the OT network, rather than running analyses on the OT network itself, to ensure that no damage is done to the network. This is made possible thanks to the complete accuracy of the Radiflow-generated digital image of the OT network and the slow rate of changes to the network, so that a days-old digital image can still be used for analysis.
CIARA’s breach-and-attack (OT-BAS) simulation engine uses the thousands of data points listed above for numerous breach and attack iterations on each and every business process and Zone, to prioritize the most impactful threats – not necessarily those with a higher probability of materializing – and prioritize the corresponding mitigation controls for these threats. Network owners are able to further customize CIARA’s mitigation plans by accounting for available security budgets over time (by quarter) and by setting additional criteria, such as preference to beef up security for high-risk zones at the expense of low-risk zones, ensuring compliance as high priority, etc.
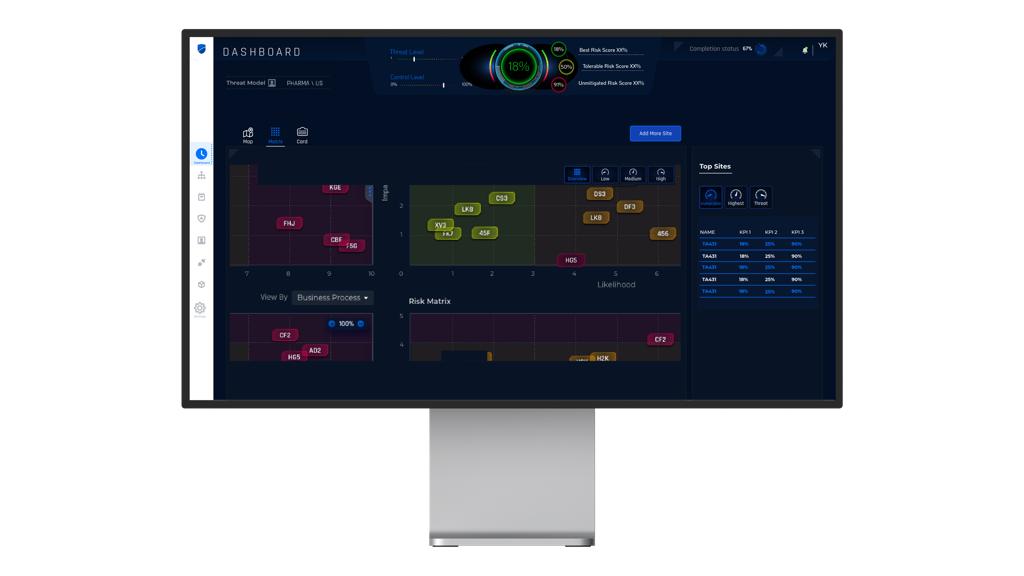
At the same time CIARA provides network owners with high-level key risk indexes for monitoring changes in risk posture. This include overall risk level, overall threat level (subject to detection of new threats and changes in attackers’ motivation) and control level, for completion of prescribed mitigation measures. Alongside these KPIs CIARA provides a host of customizable security reports used for threat mitigation and budgeting.
It’s clear to see that any project of setting up a new OT security system or improving an existing one could benefit from, and should start with a thorough risk assessment. Beyond producing a highly-optimized security plan, custom-tailored to minimize the impact of cyber-incidents by prioritizing the threats and mitigation measures most relevant to the OT network, regularly assessing and monitoring the changes in network risk allows tweaking mitigation plans based on new developments, and allows for better understanding of the organization’s threat environment by both technical personnel and decision makers.
We welcome you to schedule a personalized live demo of CIARA and of Radiflow’s entire OT security suite.
Radiflow’s CIARA industrial risk assessment and management platform enables OT organizations to maximize the value of their OT security by matching expenditure with the highest-value risk mitigation controls. The result is more and better OT security per dollar spent.

One Weak Password, Full Process Control: Inside Norway’s 2025 Dam Cyberattack

Project Management in OT/ICS Projects with IEC 62443 and MITRE ATT&CK using Radiflow

Rogue Communication Modules in Solar Inverters: Radiflow Threat Analysis