iSID, Radiflow’s Industrial Threat Detection solution, is designed specifically for the cyber-protection of industrial control systems (ICS) and critical infrastructure environments. Employed by numerous industrial companies and government organizations, it secures ICS networks, assets, and operations. Here are three major benefits of using Radiflow iSID.
Automatically learning the network topology and creating a comprehensive, visual network model, the iSID Industrial Threat Detection and Monitoring system provides operators with an accurate visualization of their OT network.
Beyond understanding the network structure, an accurate asset inventory and network-traffic map are essential for maintaining proper network hygiene and identifying potential vulnerabilities. iSID passively and unobtrusively monitors network traffic to discover network assets – from legacy to IoT. It enables drilling-down to device properties, lifecycle, and threat intelligence-derived vulnerabilities.
Compliance with standards like IEC 62443 and the NIST Cyber Security Framework require a firm understanding of security zones and conduits. A security zone is a grouping of systems and components based on their functional, logical, and physical relationships. A conduit is a logical or physical grouping of communication channels connecting two or more zones. iSID automatically identifies the zones and conduits and displays them in its network visualization.
But iSID goes much further. It also enforces thresholds. For example, let’s say a given turbine isn’t supposed to spin faster than 800 RPM. If a command is sent to increase its speed beyond this threshold, iSID will notice and generate an alert.
2. Prompt Threat Detection and Response
The earlier a threat is identified, the easier it is to remediate it.
iSID is able to detect threats and security incidents in their earliest stages. Automatically learning traffic patterns and device behavior, iSID quickly spots anomalies and other indicators of compromise such as malware and unauthorized access attempts.
Using SNORT signatures and known attack patterns and complementing these capabilities with advanced analytics and machine learning algorithms, iSID continuously analyzes network traffic and identifies deviations from normal behavior. As suspicious activities and other potential security threats are detected, iSID generates alerts and reports in real time.
iSID supports automated response actions and furnishes recommendations to help mitigate threats. Security teams can use the insights provided by iSID to develop effective response strategies, minimizing the potential impact on operations.
With such prompt detection and mitigation support, security teams can respond quickly and effectively to security incidents, minimizing the potential impact of cyberattacks on critical infrastructure and industrial processes.
3. Reduced Downtime and Disruption
iSID protects ICS environments without causing disruptions to critical operations. By detecting, identifying, and mitigating security threats early, organizations can avoid unplanned downtime and operational disruptions that result from cyberattacks and security incidents. This not only improves the overall reliability and availability of industrial systems but also helps organizations maintain a high level of resilience.
Conclusion
Radiflow iSID provides enhanced network visibility, early threat detection, and protection against cyber threats and anomalous behaviors in industrial control system environments while not hampering their operation. These benefits are crucial for safeguarding critical infrastructure, ensuring operational continuity, and mitigating the risks associated with industrial systems.
To learn more about iSID click here.
Contact us to find out more about Radiflow’s ICS security products and to assess your level of network segmentation.
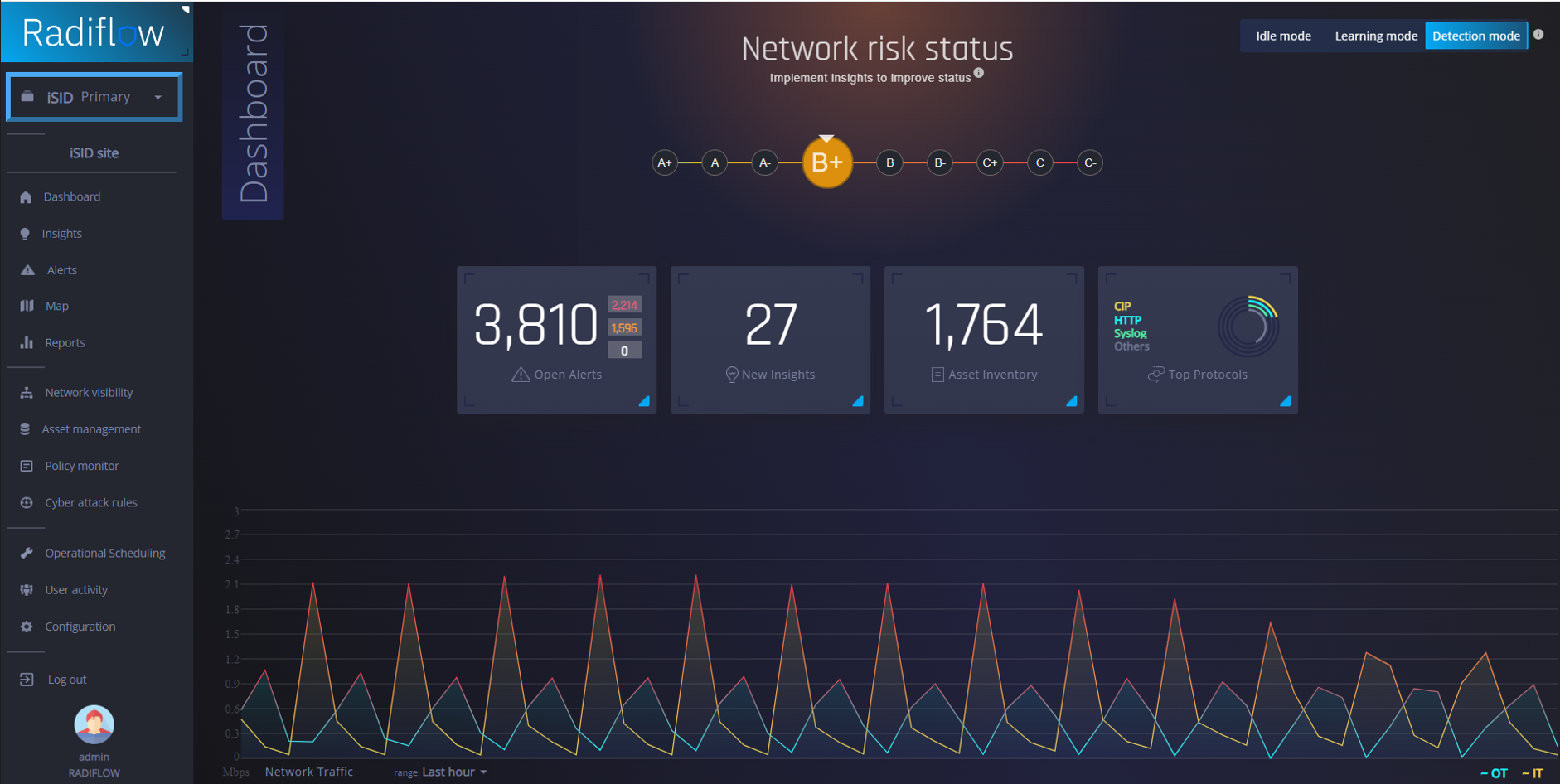
Use Radiflow iSID to detect and respond rapidly to threats in the ICS environment

One Weak Password, Full Process Control: Inside Norway’s 2025 Dam Cyberattack

Project Management in OT/ICS Projects with IEC 62443 and MITRE ATT&CK using Radiflow

Rogue Communication Modules in Solar Inverters: Radiflow Threat Analysis