Hosted by Sid Snitkin, leader of the Cybersecurity Practice at ARC, the Radiflow-ServiceNow roundtable brought together Radiflow Chief Information Security Officer Rani Kehat and ServiceNow Head of Product James Destro for a discussion on the state of IT-OT cyber-security, emerging trends in the field and the partnership between Radiflow and ServiceNow. Major among the industry trends discussed in the roundtable is the growing convergence between IT and OT security, that until recently had been seen as siloed, separate entities. As noted by Mr. Kehat, both sides of the IT-OT divide deal with intertwined technological processes, either physical or solely computational; from the point of view of the end-user organization’s security needs, labeling processes as IT or OT does not correctly describe either their MO nor their threat landscape. Today’s production processes may initiate on the enterprise side (e.g. the SAP system) and continue seamlessly in the form of OT production flow commands. As it is now, the IT-OT divide is more a matter of culture and convention: some people are in charge of IT security and others of OT security. Production organizations will have to rethink the compartmentalization between the two to better protect their systems in a holistic manner.
The roundtable also covered the Radiflow-ServiceNow integration, whereas data collected by Radiflow from remote across the entire production network, using Radiflow’s discovery tools, is correlated with and is used to enrich the ServiceNow platform’s operability. This may include, for example, obsolete or unpatched devices that pose a security risk, which couldn’t be detected by the ServiceNow platform itself.
Another major change in the cyber-security landscape is the shift from “passive”, firewall-based cyber-security, whose job is to detect early signs of an attack or breach attempt, to proactive, risk-based cyber-security. Risk management enables far more efficient allocation of security budgets based on a much broader and much more network-specific data set, including threat intelligence, the impact of a debilitating attack on different operational units, prioritization of processes by criticality and much more, all used for simulating real-world attack scenarios towards informing the client where and how they need to invest in security and (no less importantly) where not to invest, and where the client organization stands in terms of overall risk at every given moment.
Other topics discussed include the increasing popularity of MSSPs and both Radiflow and ServiceNow’s offering for MSSPs; and the current skill gap in cyber-security that has made it much harder for organizations to set up adequate security operations.
Listen to the full discussion here
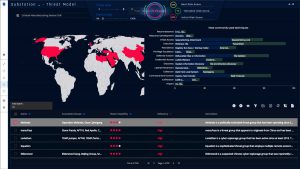
We invite you to schedule a demo of Radiflow’s solutions, to learn how it could help you to better protect your IT-OT network while optimizing your cyber-security expenditure.
I of your entire IT-OT cyber-security operation.

One Weak Password, Full Process Control: Inside Norway’s 2025 Dam Cyberattack

Project Management in OT/ICS Projects with IEC 62443 and MITRE ATT&CK using Radiflow

Rogue Communication Modules in Solar Inverters: Radiflow Threat Analysis