The UK government’s new policy to ban public sector organisations from paying ransoms to cybercriminals is a pivotal shift in the national cybersecurity landscape. Announced in July 2025, this move is aimed at cutting off the financial incentives for ransomware attacks targeting hospitals, councils, and other public bodies. While the intention is strategic, the implications for OT cybersecurity—particularly in ICS environments used in public utilities and infrastructure- are significant.
Operational Technology (OT) systems—such as those controlling water treatment, energy grids, and transport—are often part of the public sector. Many of these systems:
A successful ransomware attack can halt physical processes, damage assets, and endanger public safety. With ransom payments banned, these systems must be hardened further—there’s no financial fallback.
IEC 62443-3-2 recommends conducting a risk assessment to prioritise which systems require protection based on potential operational impact. For public sector OT environments, this involves:
Zones supporting public safety or critical services should be designed to meet SL 3 or higher, requiring strong access control, authentication, and monitoring.
ICS and OT networks in the UK face persistent threats from both cybercriminal groups and nation-state actors. Key characteristics of the current threat landscape:
Attackers often conduct long-term reconnaissance, remain dormant, and then deploy destructive payloads—making recovery difficult and expensive if not well-prepared. UK ICS operators are also seeing more “double extortion” tactics, where attackers not only encrypt files but also steal data to pressure organisations into paying.
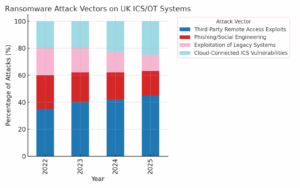
*The changing share of attack vectors over the past four years.
The average ransomware demand against public sector entities in the UK has reached six to seven figures per incident. That’s before counting:
By contrast, building basic cybersecurity hygiene—segmentation, access control, backups, and detection—typically costs a fraction of a single ransom demand.
£100,000 spent on preventive controls is far cheaper than £1.5M lost in ransom + recovery + downtime.
Cybersecurity is now an operational cost of running OT—not an optional insurance.
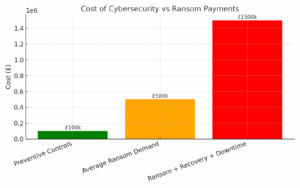
*How prevention costs compare to ransom and recovery expenses
Instead of relying on ransom payment as a last resort, public sector bodies must invest in:
In 2023, a UK water supplier experienced a ransomware attack that disabled its SCADA systems for 48 hours. Had the ransom payment been banned then, operations would’ve stalled longer. Applying IEC 62443-2-1 guidelines—particularly strong incident response, offline backups, and vendor response SLAs—could have cut downtime to under 24 hours.
Under NIS2 and OES incident reporting rules:
This elevates the importance of compliance with IEC 62443-2-1 (policy, roles, incident management) and -2-4 (secure integration by vendors).
The ransomware payment ban signals a clear policy shift: recovery, not ransom. For public sector OT and ICS operators, this means stronger engineering discipline, regular drills, and alignment to standards like IEC 62443, NIS2, and NIST SP 800-82r3.
Spending on proactive cybersecurity controls is not only more effective—it’s cheaper than crisis recovery.


Hacktivists Are Hijacking Exposed ICS Devices — Here’s What Every Operator Must Know

The JLR Cyber Incident: A Wake-Up Call for Manufacturing Resilience

New Radiflow360 platform to offer visibility, control across OT cybersecurity lifecycle