What better way to start 2024 than a recap of what happened in 2023! Let’s have a look at some of the highlights from our partner, Fortinet’s 2023 State of Operational Technology and Cybersecurity Report to assess the trends.
Significant Improvements, But…
While the number of organizations that did not incur a cybersecurity intrusion improved dramatically YoY – from 6% in 2022 to 25% in 2023 – there is still significant room for improvement. After all, three-fourths of OT organizations reported at least one intrusion during the last year. In addition, about one-third of respondents reported being victimized by a ransomware attack (unchanged from 2022) while intrusions from malware and phishing increased 12% and 9%, respectively.
Attack Surface is Expanding
When a cyberattack occurred last year, nearly one-third (32%) of respondents indicated that both IT and OT systems were impacted—up from only 21% last year. The growing integration of IT and OT networks and data account for the increase. We expect more of it in the year ahead.
To combat intrusions, OT security professionals are upgrading the cybersecurity solutions and services in their industrial networks. Investments in cyber defenses grew in direct proportion with the volume and intensity of OT threats and cyber actor activities. That’s a good sign.
2023 Was a Busy Cyber Year Across the Board
The cost of successful cyberattacks continues to escalate. Here are examples of major attacks and their financial and other effects on ICS/OT/industrial enterprises over the past year:
Recommendations for Surviving the Cyber Wars in 2024
The pressure on the security of industrial and critical infrastructure operations is getting stronger. What should you do to survive in the highly competitive battle against cyberthreat actors especially in light of the impending NIS2 Directive and new SEC cyber regulations?
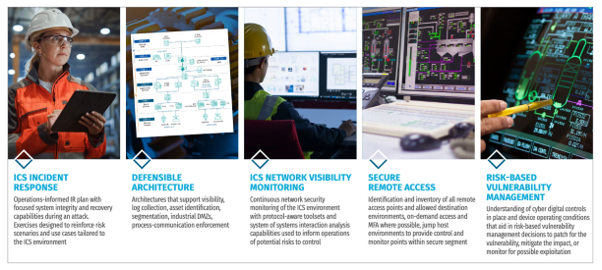
SANS – Five ICS Cybersecurity Critical Controls
3. Contact a Radiflow OT Security Expert to help you assess and manage risk in your OT environment according to the requirements of NIS2, IEC62443, etc.
Radiflow’s data-driven CIARA uses Machine Learning and other AI techniques to simulate hundreds of commonly-used security controls against relevant known threats, factored against common OT risk scenarios such as loss of availability, loss of control, damage to property, etc. CIARA quantifies the risk of a given attack to your operations and recommends the most cost-effective mitigation measures.
How close are you to NIS2 and IEC62443 compliance? What should you do to close the gaps? CIARA will figure it out and tell you.
In the dynamic OT risk environment, once-a-year risk assessments are not enough. CIARA is automatic and works fast. You can run it as often as you like.Your organization can deploy the CIARA Risk Management solution or engage Radiflow’s Risk Management Services to run CIARA for you while you enjoy the cyber-risk benefits.
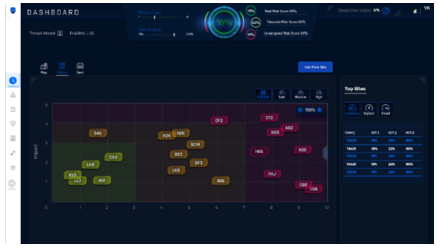
CIARA calculates and displays risk per site and overall
4. Implement a leading threat detection platform to monitor and protect your operations.
The Radiflow OT threat detection and monitoring platform, iSID, is designed specifically for the cyber-protection of industrial control systems (ICS) and critical infrastructure environments. Deployed by numerous industrial companies and operators of critical infrastructure, iSID continuously secures ICS networks, assets, and operations, delivering:
Your organization can deploy iSID or engage Radiflow’s MDR Services to run it for you remotely.
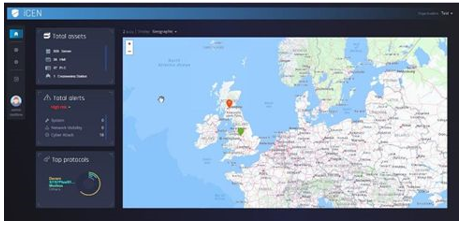
Monitor the cybersecurity of all your sites from a central location
A Secure 2024
The trends are clear: more cyberthreats and more regulations requiring an increasingly robust security posture. We’re here to help with leading solutions and services. Contact Radiflow to secure your operations, minimize risk, and comply with the new regulations.

Let’s Ring in a Cyber Safe and Secure 2024

One Weak Password, Full Process Control: Inside Norway’s 2025 Dam Cyberattack

Project Management in OT/ICS Projects with IEC 62443 and MITRE ATT&CK using Radiflow

Rogue Communication Modules in Solar Inverters: Radiflow Threat Analysis