With the constant increase of cyber attacks on Industrial entities and Critical infrastructures, it’s clear industry sectors around the world are susceptible to a variety of attacks, and last Monday (June 27, 2022) it happened in a steel plant in Iran- as part of the escalating cyber warfare tensions worldwide. Attacks on industrial infrastructure have been continuous in the Middle East. During the past year we witnessed cyber attacks on petrol stations, camera systems in Iran, and last week an attack on local “alert systems” in Israel.
One of Iran’s major steel companies claimed it was forced to halt production after being hit by a cyberattack, making it one of the biggest assaults on the country’s strategic industrial sector in recent years.
The state-owned Khuzestan Steel Company, which is currently under U.S. sanctions, said experts had determined the plant had to stop work until further notice “due to technical problems” following “cyberattacks.” So far the company has not blamed any specific group for the alleged attack.
In Twitter, the hacking gang named Gonjeshke Darande, which has claimed responsibility for previous attacks on Iranian infrastructure has subsequently posted a video on Twitter, stating that it had hacked Khuzestan as well as two other steel plants. The gang continued and published not only a video of the machine explosion, but also pictures of the HMI (the user interface or dashboard that connects a person to a machine, system, or device), as well as a picture of the network
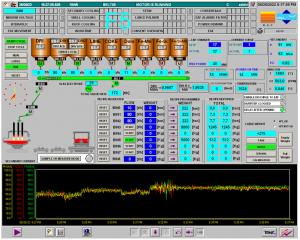
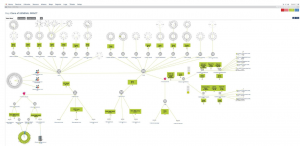
[Twitter source – https://bit.ly/3HYVInd].
Our Radiflow experts and analysts shared a few insights about this incident.
For one, the intrusion vector is still unknown so we don’t know which vulnerability was exploited to gain access. It’s important to mention (although we see this over and over again), most OT infrastructures are not well segmented, neither protected well enough from connected IT networks/environments. In addition to that, outdated/unpatched operating systems of OT servers and workstations of SCADA and DCS environments combined with the lack of IDS (intrusion detection systems) which can detect early signs of suspicious activity, contributes to easy adversarial lateral movement within the plant.
Even in the event that the attackers do obtain access, it’s still not an easy task to execute an attack. They need to have a domain expert, so they can create the desired effect, in the desired time and place (like was shown in the footage- assuming it is authentic).
Another issue worth pointing out is the relation between the attack on the ICS and the attack on the plant CCTV systems. The breach and further full control over the CCTV cameras allowed hackers to achieve a number of goals – validate and control the physical effects, exfiltrate the footage and post it later as a proof for demonstration purposes and show the vulnerability not only of OT environments but of physical security systems as well.
Lastly, and important to mention, is network visibility. This is critical for the attackers, as well as for the defender/s. The network diagram posted by the hacking group shows that the knowledge of network connectivity and its vulnerabilities is playing a critical role for hacking activities and more than that for defensive operations.
Radiflow is expecting for further exploitation of critical infrastructure and strategic manufacturing facilities worldwide by various hacking groups from various reasons therefore proper and correct implementation of various cyber security tools for industrial environments which include OT network visibility, intrusion detection, virtual breach-attack-simulation and in general risk management is a vital part of organizations’ strategy in strengthening their cybersecurity posture.

One Weak Password, Full Process Control: Inside Norway’s 2025 Dam Cyberattack

Project Management in OT/ICS Projects with IEC 62443 and MITRE ATT&CK using Radiflow

Rogue Communication Modules in Solar Inverters: Radiflow Threat Analysis