Project management in OT/ICS is the structured execution of engineering, automation, and cybersecurity initiatives within industrial environments.
These projects have a clear start and end point, and typically deliver a service or result, not just a product. In this context, managing an OT cybersecurity project aligned with IEC 62443 or NIS2 involves more than technical execution—it requires professional project governance across all five phases:
This includes projects like:
Unlike IT projects, OT/ICS project management must consider:
It typically involves a mix of IT, engineering, OT personnel, and vendors, working under tight schedules and high uptime requirements.
Goal: Define Success for Stakeholders
For project sponsors, success is not just “deploy firewalls” or “upgrade ICS.” The true goal of an OT cybersecurity project is to mitigate cyber risks, meet compliance, and improve resilience, while staying within scope, time, and budget.
Deploy network segmentation and firewalls in a manufacturing site to meet IEC 62443-3-3 requirements, and by that reduce cyber risk exposure, ensure regulatory approval, and achieve a Cost Performance Index (CPI) above 0.9.
Stakeholders & the RACI Matrix
OT projects often involve multiple parties: internal IT/OT teams, external vendors, engineering, and compliance personnel. Collectively, these are your stakeholders. To manage expectations and accountability, apply a RACI matrix:
Using a RACI chart helps the Project Manager define roles clearly and reduces friction during execution and escalation.
Use of EVM – Emphasizing Scope Over Progress
When applying Earned Value Management (EVM), emphasize scope delivery rather than just activity completion. Many projects look “busy” but deliver little actual value. For example:
“Only 35% of the defined scope was completed, even though 55% of the budget was spent.”
This reframing promotes accountability and aligns with compliance requirements where actual control implementation (e.g., SR 1.2 for firewall rules) is the metric, not task progress alone.
Earned Value Management (EVM) brings discipline and visibility to OT/ICS projects by linking schedule, budget, and progress into measurable indicators.
In OT/ICS, you don’t get infinite test environments or rollback buttons. So, you need to know if your project is working not guess. That’s why EVM is essential.
Earned Value Management (EVM) is a proven method for tracking cost and schedule performance in complex projects. When applied to OT (Operational Technology) and ICS (Industrial Control Systems) environments especially those governed by IEC 62443 standards EVM can reveal where delays and overruns pose security, operational, or compliance risks.
These metrics let you track:
Project goal: Deploy network segmentation and firewalls in a manufacturing site to meet IEC 62443-3-3 requirements.
Results:
Delays in this OT project directly impact the implementation of critical IEC 62443 security requirements:
| IEC SR | Description | Cybersecurity Needs |
| SR 1.1 | Network segmentation between zones | Unrestricted data flow between zones |
| SR 1.2 | Firewalls/conduits between zones | No communication control |
| SR 3.1 | Authenticated communications | Unverified device access |
| SR 5.2 | Zone access enforcement | Remote access to critical systems |
Delaying segmentation and firewall deployment exposes the OT environment to these attack techniques:
| Technique ID | Name | Exposure Risk | IEC Link |
| T0837 | Remote Services | Remote access pivots into control | SR 1.2 |
| T0806 | Valid Accounts | Enables lateral movement | SR 3.1 |
| T0887 | External Remote Services | VPNs/DMZs become breach vectors | SR 1.1 |
| T0859 | Commonly Used Port | Predictable traffic is easily scanned | SR 1.2 |
| T0810 | Exploitation of Remote Svcs | Potential remote code execution | SR 1.2 |
CIARA isn’t just a risk management tool; it’s a security management platform, project tracking system, and cost optimization solution. By tracking schedule and cost performance alongside IEC 62443 maturity and known threat vectors (via MITRE ATT&CK), you gain a comprehensive view of project health, risk, and compliance posture.
The Radiflow CIARA Risk Prioritization and Compliance Platform combines:
…to create a smarter, more secure OT cybersecurity program.
Mapping project progress and costs with CIARA’s risk-based asset and control assessments is straightforward. CIARA is designed for IEC 62443-aligned risk assessments, so integrating EVM offers measurable tracking for implementation.
In CIARA, each risk treatment (e.g., segmenting a network, implementing SR 1.2 controls, hardening remote access) becomes a trackable project activity.
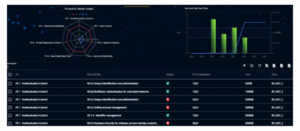
CIARA allows you to score threats and residual risk based on control effectiveness. EVM provides a real-world performance view of implementation.
| Risk Area | CIARA Prioritization | EVM View | Target |
| Remote Access (T0887) | Medium risk | CPI = 0.6, SPI = 0.7 | Zone 1 – 7PLC, 2HMI |
| Network Segmentation (SR 1.1) | High risk | CPI = 0.9, SPI = 1.0 | Zone 2,3 – 12PLC, 4HMI |
| Vendor Access Controls | Low risk | SPI = 0.4 | Zone 4 – 3 EngStation |
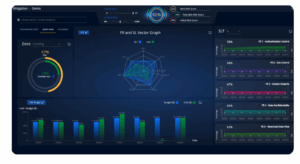
CIARA generates risk reports and compliance maps for IEC 62443, NIS2, and more, detailing cost and implementation status for each site, zone, and security requirement.
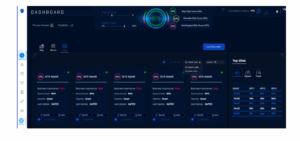
Merging the experience in the real project of OT Cyber Risk Management and compliance assessment with Radiflow, the time spent to create an overall view of the current environment and track activity by activity to achieve the result of the project.
From zero to target, Radiflow makes it very easy and accurate the work of the Project Manager to follow these guidelines:
Radiflow monitors the network and provides new TI information consistently to identify any useful change and evidence to resize the project, driving the PM to easily follow the Agile process or a similar common flexible Project Management Framework, keeping in consideration the following point:


Project Management in OT/ICS Projects with IEC 62443 and MITRE ATT&CK using Radiflow

Rogue Communication Modules in Solar Inverters: Radiflow Threat Analysis

Securing Legacy Utility Substations with Garland Technology and Radiflow